NIST SP 800-53 Compliance & Control Mapping
Accelerate authorization and strengthen security with comprehensive NIST 800-53 consulting, NIST readiness assessments, 800-53 testing, and RMF package support. Additionally, we map controls to related frameworks—NIST 800-171, CMMC, and NIST CSF 2.0—so you can streamline compliance across your environments. .
- 800-53A assessment: interviews, examination, testing
- RMF artifacts & A&A package support
- Control inheritance & FedRAMP mappings
- Crosswalks to 800-171, CMMC, CSF 2.0
NIST Consulting Services
Level up your security program with NIST Consulting Services designed for regulated environments, including federal, defense, and healthcare organizations. First, we align your systems to NIST SP 800-53 and the Risk Management Framework (SP 800-37) end-to-end, from readiness through authorization. As a result, you accelerate ATO timelines, reduce audit friction, and harden controls across both on-prem and cloud environments. Moreover, we map NIST controls to related frameworks—800-171, CMMC, and CSF 2.0—to further streamline compliance while maintaining strong, evidence-backed security. Ultimately, you gain clear documentation, prioritized POA&Ms, and measurable, risk-based improvements to your overall security posture.
- Control Implementation & Hardening: AC, AU, CM, IA, IR, MP, PE, PL, PS, RA, SC, SI, etc.
- NIST 800-53 Readiness Assessment: Test procedures, sampling, and evidence collection.
- RMF Support (SP 800-37): Categorization, selection, implementation, assessment, authorization, monitoring.
- Control Inheritance: FedRAMP/cloud service mappings and shared responsibility models.
- Policy & Procedure Development: Program-level and system-level documentation.
- POA&M Management: Risk-based remediation planning and status reporting.
Control Mapping & Framework Harmonization
Reduce duplicate effort by aligning NIST 800-53 controls with related obligations:
NIST 800-53 ↔ NIST 800-171
- Map derived NIST 800-171 requirements to NIST 800-53 controls
- Identify gaps and compensating controls
- Artifact reuse strategy
NIST SP 800-53 ↔ CMMC
- Practice alignment and maturity expectations
- Assessment prep checklists
- Evidence cross-reference
800-53 ↔ CSF 2.0
- Program outcomes & metrics
- Identify/Protect/Detect/Respond/Recover mapping
- Continuous improvement
Our 800-53 Assessment Process
Scope & Categorize → Select → Implement & Document → Assess (53A) → Authorize → Monitor
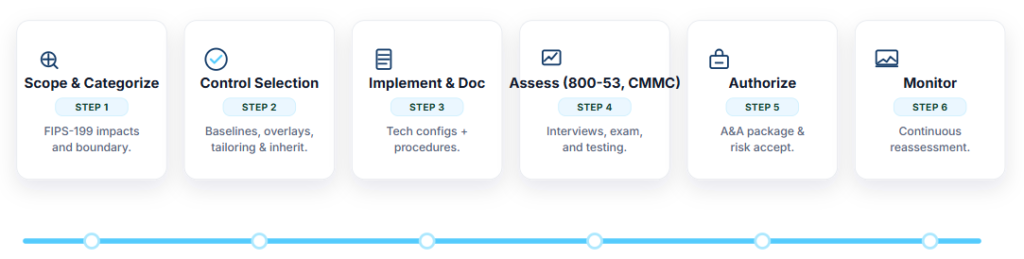
Our NIST 800-53, CMMC, and RMF Assessment Process
First, our assessment and authorization process follows the NIST Risk Management Framework (RMF) to ensure your organization achieves defensible NIST 800-53 compliance while supporting CMMC readiness and ongoing risk management. Rather than treating compliance as a one-time audit, we apply a structured lifecycle approach that aligns technical controls, documentation, and risk decisions from initial scoping through continuous monitoring.
Scope & Categorize
To begin, we define system boundaries, data types, and environments while determining FIPS 199 impact levels. This step ensures the correct NIST 800-53 baseline is applied and prevents unnecessary controls that slow authorization or increase cost.
Control Selection
Next, we select and tailor NIST 800-53 controls based on system impact, overlays, and inherited controls. At this stage, we align controls with CMMC and other applicable requirements, establishing a foundation for framework harmonization and evidence reuse.
Implement & Document
Then, we support control implementation and documentation, including technical safeguards, policies, procedures, and System Security Plan (SSP) narratives. These artifacts form the core of your RMF package and are written to support both authorization and future assessments.
Assess (NIST 800-53 & CMMC)
After implementation, we assess control effectiveness using NIST 800-53A test procedures. Through interviews, examinations, and technical testing, we validate evidence and identify gaps. As a result, assessment outputs can be reused across RMF package support, authorization and CMMC readiness activities.
Authorize
Next, we assemble and support the authorization package, including the SSP, SAR, POA&M, and risk documentation. This step enables informed risk acceptance decisions and supports ATO readiness through complete, defensible RMF artifacts.
Monitor
Finally, we establish continuous monitoring processes to maintain compliance over time. This includes control tracking, evidence updates, and reassessments to support ongoing authorization, CMMC sustainment, and continuous improvement.
Together, these steps create a scalable, repeatable compliance lifecycle that aligns NIST 800-53, RMF, CMMC, and NIST CSF requirements while reducing audit fatigue and long-term risk.
Why This Process Works
RMF-Aligned from Day One
Our process mirrors NIST SP 800-37, ensuring every activity directly supports authorization and continuous monitoring.Built for CMMC and NIST CSF Overlap
We intentionally map controls and evidence so NIST 800-53 work supports CMMC practices and CSF outcomes—eliminating duplicate effort.Evidence Reuse, Not Rework
Documentation and artifacts are created once and reused across assessments, audits, and certifications.Risk-Based, Not Checkbox Compliance
We prioritize real risk reduction, helping leadership make informed decisions while staying audit-ready.Designed for Long-Term Compliance
From ATO support to continuous monitoring, this process scales as your environment and requirements evolve.
Deliverables & Outcomes
Control Worksheets & NIST 800-53 Results
Test procedures, sampling notes, evidence references, and results per control/objective.
Policies, Procedures & Standards
Program and system documentation aligned to selected baselines and overlays.
Authorization Package
RMF artifacts (NIST SP 800-37), risk register, ATO support materials, and decision memos.
POA&M with Risk-Ranked Fixes
Gap list, severity, owners, timelines, and status reporting cadence.
Framework Mapping Matrix
NIST 800-53 ↔ NIST 800-171 ↔ CMMC ↔ CSF crosswalk for evidence reuse and audit prep.
FAQs
What impact level do I need?
We help apply FIPS-199 to determine Low/Moderate/High and tailor controls accordingly.
Can you reuse FedRAMP or cloud controls?
Yes—inheritance reduces duplicative effort when documented with clear responsibilities and evidence.
Do you support ongoing monitoring?
Yes—metrics, scan cadence, and periodic control assessments keep authorization current.

