Identify, classify, prioritize, remediate, and mitigate software vulnerabilities effortlessly with our vulnerability management program.
Manage The Process
It all begins with a practical way to identify, classify, mitigate, and remediate vulnerabilities for our clients as part of our Vulnerability Management program. Without an effective vulnerability strategy, your organization may find problems after your systems have been compromised. That is why we offer practical ways to discover, prioritize, and report these vulnerabilities to our clients as part of a VM Program. Whether the culprit is patch management, changes in network security policy, or reconfiguration of software/applications, having a solid program in place that allows for monitoring of vulnerabilities through every step of the process is crucial to the overall security posture of your organization.
We believe in a cyclical approach to vulnerability management. Our team will work alongside yours to make sure your organization is correctly implementing a vulnerability management program. With extensive experience in the IT Security industry, our engineers work with our clients to implement an affordable and sustainable vulnerability management program that is easy to implement and effective at handling the ever-changing network landscape. Praetorian Secure offers the knowledge and support to make a positive impact on the way your organization handles vulnerabilities. With the implementation of our proven vulnerability management program and by taking advantage of our On-Demand Vulnerability Scanning, our clients operate with the peace-of-mind that their environment is secure and easy to manage.
Vulnerability Management Program Vs Vulnerability Assessment
In short, Vulnerability Assessment is about identifying vulnerabilities, while Vulnerability Management is a comprehensive and ongoing process that actively reduces security risks.
Vulnerability Management:
- Identifies, prioritizes, remediates, and monitors vulnerabilities.
- Encompasses the entire vulnerability lifecycle.
- Involves ongoing processes for risk assessment, remediation, and monitoring.
- Is an ongoing and iterative process.
The main goal of Vulnerability Management is much broader and involves not only identifying vulnerabilities but also actively managing and reducing overall cybersecurity risk.
Vulnerability Assessment:
- Identifies and catalogs vulnerabilities.
- Provides a snapshot of the current state of vulnerabilities.
- Involves automated scans and assessments.
- Usually performed periodically.
The main goal of a Vulnerability Assessment is to identify vulnerabilities within an organization’s systems, networks, or applications.
Vulnerability Management Program Overview
Program Benefits
Methodical Approach
Our Vulnerability Management program follows a structured and methodical approach, ensuring every aspect of your organization’s cybersecurity is systematically assessed. This meticulous process allows us to identify, prioritize, and address vulnerabilities with precision, reducing the risk of potential threats.
Improve Business Productivity
By proactively managing vulnerabilities, your organization can focus on core business operations without the disruptions caused by security incidents. A secure environment fosters a more productive workforce, leading to enhanced business efficiency and growth.
Peace Of Mind
With our comprehensive Vulnerability Management program in place, you can enjoy the peace of mind that comes from knowing your digital assets are well-protected. Our continuous monitoring and risk mitigation efforts provide you with confidence in your cybersecurity posture, allowing you to concentrate on your business goals.
Faster Incident Response
With a proactive approach to vulnerability management, your organization can respond more swiftly and effectively to security incidents when they occur.
Vulnerability Management Program Vs Vulnerability Assessment
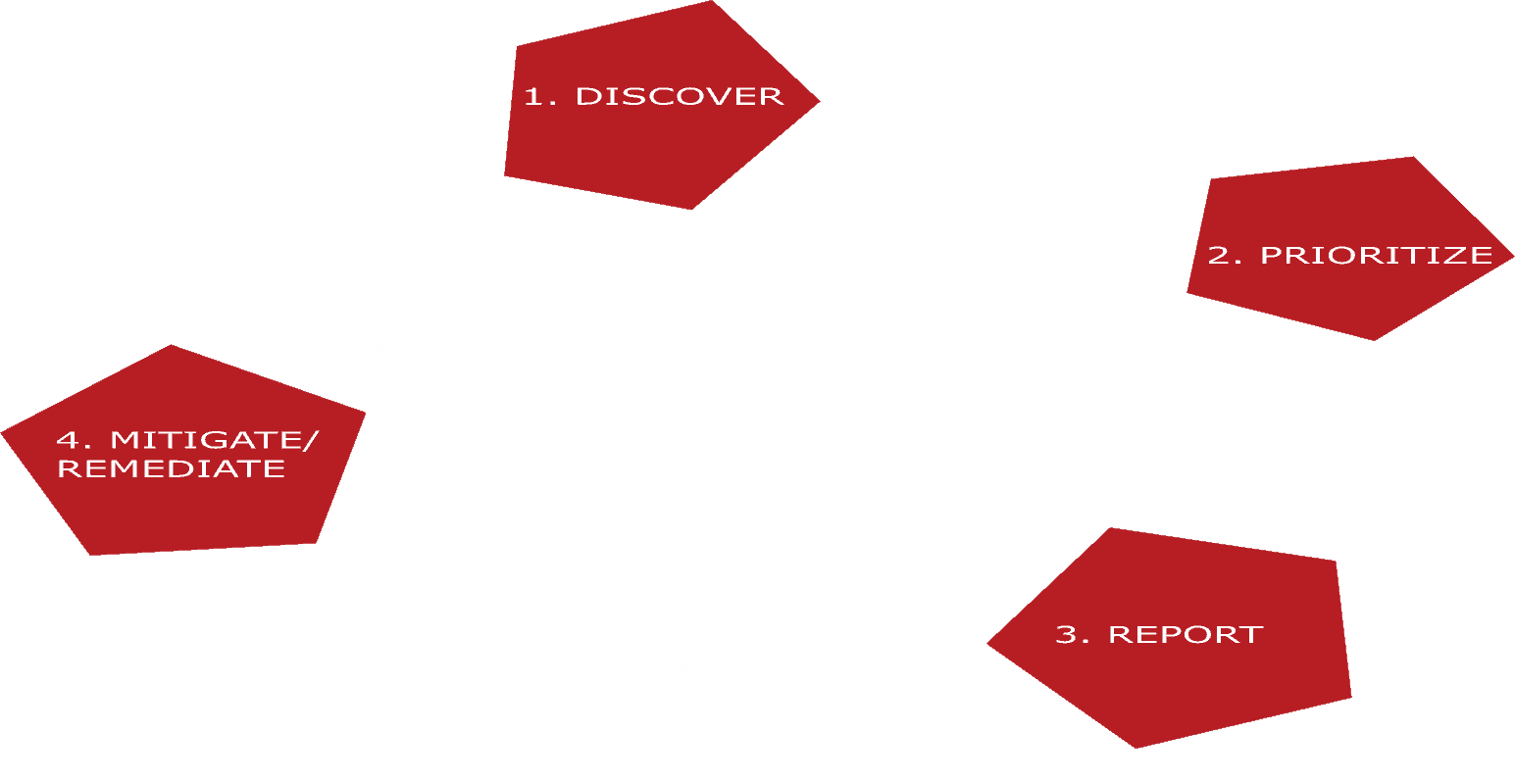
Our comprehensive Vulnerability Management program follows a structured, four-step approach:
- Discover: We proactively identify vulnerabilities in your digital assets, systems, and networks, using advanced scanning tools and techniques.
- Prioritize: Each vulnerability is meticulously assessed to determine its severity and potential impact on your organization’s security. This prioritization guides our focused efforts.
- Report: Clear and actionable reports are generated, providing you with insights into your security landscape. We ensure transparency in our findings and recommendations.
- Mitigate/Remediate: Swift and effective action is taken to address identified vulnerabilities, including patching, configuring, or implementing mitigation controls.
- (post-process step) Improve: Continual monitoring and analysis are conducted to track progress and address emerging threats, enhancing your overall cybersecurity resilience.
Our Vulnerability Management program ensures that your organization stays ahead of potential risks, safeguarding your digital assets and maintaining a robust security posture. In addition, we used the OWASP Vulnerability Management Guide and our past experience to help develop of current approach (which is always evolving and being updated).
Resources
Documents
Blogs
Videos
Let Us Help You Implement A Successful Vulnerability Management Program Today!
We are here to service your needs. Contact us today for more information about our Vulnerability Management Assessment Services.