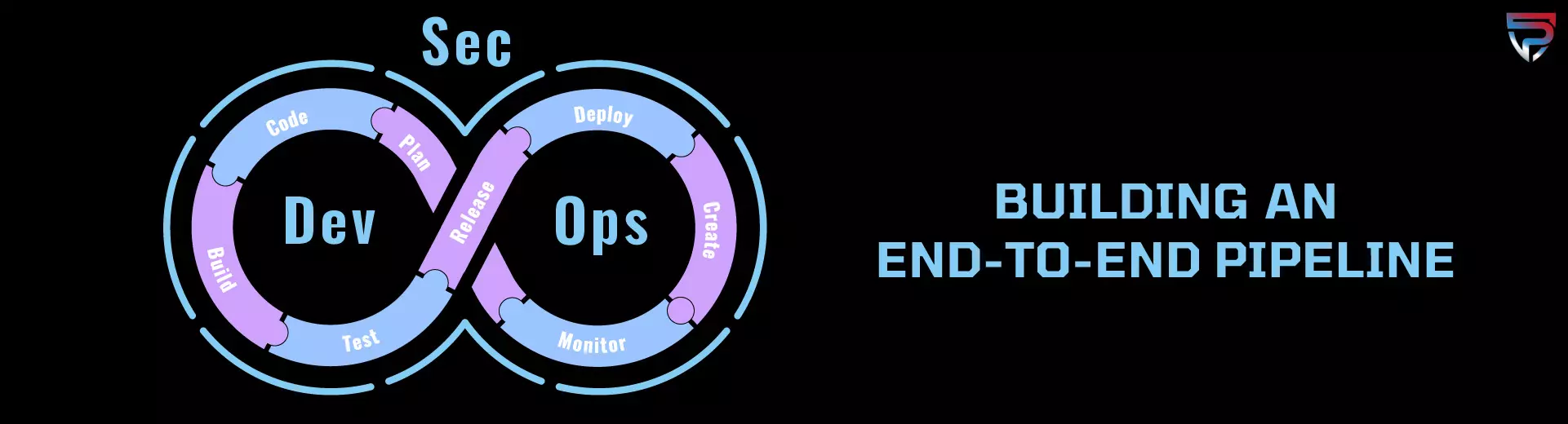
Building an End-To-End DevSecOps Pipeline: Overview
We will define what a DevSecOps CI/CD Pipeline is, what the main goals should be, benefits, and how to implement DevSecOps into the pipeline most efficiently. Then, we will cover examples of the two most common application services to build an End-To-End CI/CD DevSecOps Pipeline with. They are Microsoft Azure – Part 2 and AWS (Amazon Web Services) – Part 3.
When organizations are developing new applications, they should focus their energy on integrating DevSecOps into the Software Development Life Cycle (SDLC). Otherwise referred to as “shifting left” or being more agile but also completing security testing. Which is best done early and often in the software development life cycle. Specifically, creating a more secure CI/CD Pipeline in the long haul. It may just take some time to get used to a new way of doing things at first, but it will be highly rewarding once mastered.
For those who are not familiar, a CI/CD Pipeline is, “a series of steps that must be performed in order to deliver a new version of the software. Continuous integration (CI)/continuous delivery (CD) or CI/CD pipelines are a practice focused on improving software delivery, quality, and security. Keep in mind that quality defects can lead to security weaknesses and vulnerabilities. Combining CI/CD At Praetorian Secure we offer complete DevSecOps services from strategy and testing to the delivery of key reports and milestones. This blog series will focus on building an End-To-End DevSecOps Pipeline. Including part 1/3 an overview, part 2/3 Microsoft Azure specifics, part 3/3 AWS specifics.
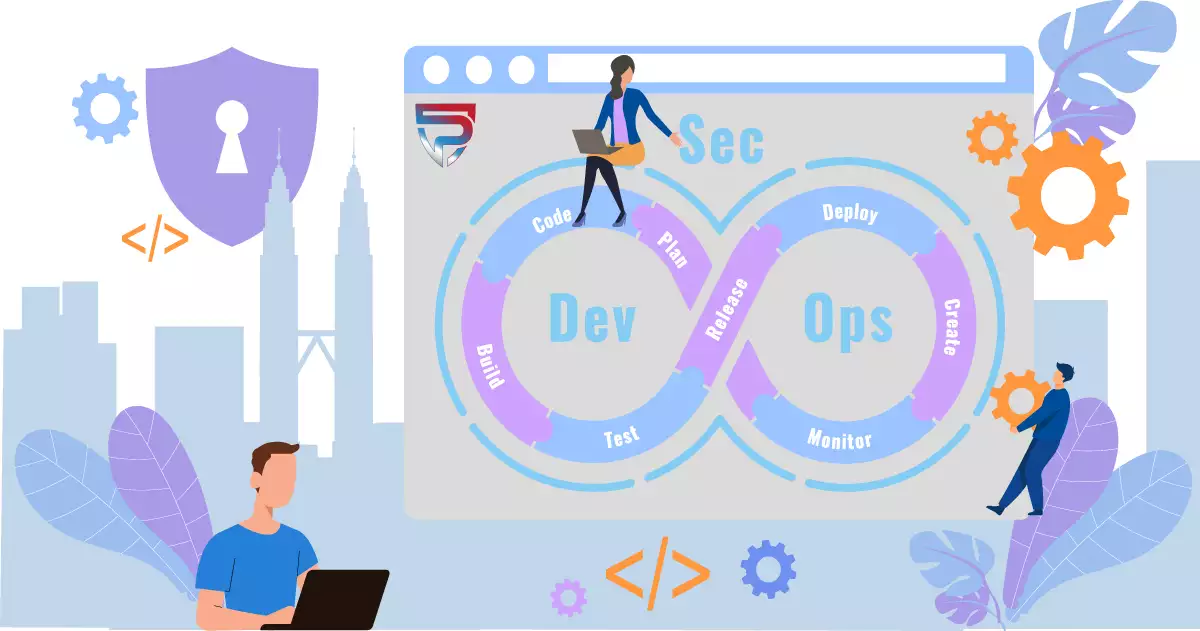
The DevSecOps Pipeline
A DevSecOps CI/CD Pipeline is used to help developers implement new ideas quickly without overlooking security. To simplify, DevSecOps is just a development pipeline with integrated security practices and tools performed repeatedly after each stage. It is best to start integrating these practices into the pipeline as soon as possible. The reason is, it will benefit your organization in the long term by reducing cost and shortening your development lifecycles while simultaneously improving security. Creating a more agile framework along the way. One where developers, application stakeholders, project leads, and security teams can work together seamlessly, at an optimal pace. Uncoordinated efforts amongst teams can derail a DevSecOps Pipeline in a hurry.
Goals & Objectives
Each year application development teams face tremendous pressure to build new, better applications faster than the year prior. With the thought of creating a DevSecOps CI/CD pipeline, the main goal is to minimize risk and prevent new threats from entering the DevOps pipeline. It is self-explanatory. The objective is to improve the agile framework by surrounding it with security. In essence, this makes the speed of development and the security of code equivalent in priority. Whereas, before they were opposites, and you could not get both at once. The good news is our DevSecOps engineers can help you solve this problem by developing a custom DevSecOps solution for your organization.
Benefits of DevSecOps Integration
It allows developers the ability to make multiple revisions over a short time frame to meet the rapid deadlines without sacrificing code security quality. This is accomplished by automation of the CI/CD Pipeline, therefore, reducing manual interactions and time spent reviewing said interactions.
The benefits of adding security into the DevOps pipeline includes:
- Testing early and often reduces development costs for remediation.
- Quickly ID security vulnerabilities.
- Improved development speed & security for teams.
- Patch vulnerabilities much faster than before.
- Secure software is developed early on.
- Change in groups mindset, now security is a priority.
- Faster recovery speed in the event of a security incident.
- Long-term confidence and satisfaction.
- Reduced cost of remediation and improved app quality.
- A cost-effective strategy for modern applications.
- Give your team a competitive advantage.
Another benefit of integrating DevSecOps into SCLC is that modern DevOps Security was built for containers and microservices.
Microservices are described as, “an architectural pattern of composing a distributed application from separately deployable services that perform specific business functions and communicate over web interfaces” (Microsoft). DevOps teams use microservices as building block to put together larger systems, speeding up the DevOps Pipeline. A common pattern we are seeing today is the use of container clusters to implement microservices. This is something we as DevSecOps engineers can applaud.
DevSecOps Kubernetes and Docker Containers
Any great DevSecOps pipeline being developed today uses containers and microservice. A container or containerization in DevOps is referring to placing a software component and its environment, dependencies, and configuration, into an isolated unit, called a container. This makes it possible to deploy applications consistently across any computing environment. For instance, it could be on-premises or cloud-based. When it comes to the debate on Kubernetes vs Docker the answer is simple, both. These tools have great synergies when used together correctly and rapidly improve development speeds and ability to build, deliver, and scale containerized apps through automation.
In summary, you can use Kubernetes and Docker together to:
- Create more scalable applications.
For example, if your app load increases all you need to do is spin up more containers or add more nodes to your Kubernetes cluster.
- Make your infrastructure more robust and your app more highly available.
For example, your app will remain online, even if some of the nodes go offline. Which is always a good thing no one wants an application to go offline that is in production.
Docker provides an open standard for packaging and distributing containerized applications. Using Docker, you can build and run containers, and store and share container images. Kubernetes is open-source orchestration software that provides an API to control how and where those containers will run. By implementing Kubernetes plus Docker containers into the DevOps Pipeline you can achieve the balance between speed, security, and deliver of code faster that is scalable.
DevSecOps Tools
Choosing the right DevSecOps tools for your CI/CD Pipeline can be a big decision. There are a lot of crucial factors to weigh such as acceptance, ease of integration, existing system/network, costs, etc. Some popular DevSecOps tools include:
Vulnerability Scanning Tools
- Static Application Security Testing (SAST) Tools – WhiteSource, Codacy, SonarQube, Acunetix, GitLab, Aqua Security, Snyk, XebiaLabs, and more.
- Dynamic Application Security Testing (DAST) Tools – OWASP ZAP, Burp Suite Professional, Jenkins, Acunetix, Nikto, Detectify, Netsparker, and more.
- Software Composition Analysis (SCA) Tools – Snyk, WhiteSource, GitLab, GitHub, Black Duck, Fortify, Veracode, and more.
- Monitoring – AppDefender, ArcSight, Data Dog, Logz.io, Honeycomb and more.
Featured Tool
- Fortify Static Code Analyzer (SCA) – uses static and binary analysis to identify where secure code standards are not implemented leading to security weaknesses, vulnerabilities, and quality issues. Furthermore, when submitting a medical device to the FDA for premarket approval with safety concerns you must be aware of quality and safety issues that can impact patient care. That is why integrating DevSecOps into the SDLC is even more important for medical devices and supporting applications.
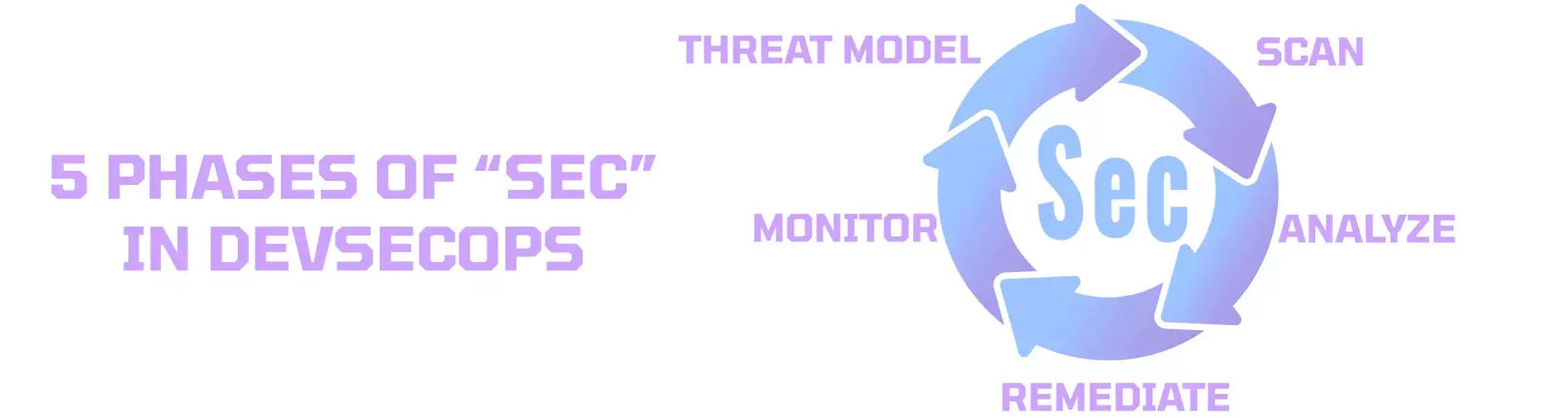
5 Phases of “Security” in DevSecOps
There are five phases of security in the DevSecOps pipeline that are used continuously throughout the SDLC until an application reaches production approval. The phases are as follows:
- Threat Modeling: Come up with all possible attack scenarios, understand how data flows, test to identify vulnerabilities, and discuss mitigation strategies.
- Scan: Use SAST and/or DAST tools to test your application’s executed code or source code for vulnerabilities before an attacker does.
- Analyze: Review and consolidate scanning reports. Decide if the vulnerability is accurate or a false positive. Decide on how to remediate the vulnerability and document recommended solution.
- Remediate: Speak with Developers and project leads and determine fix action for all vulnerabilities reported in order of highest severity to lowest.
- Monitor: Determine metrics then try to reach or exceed milestones. Re-assess and repeat. Continuous monitoring is the focus.
How to Implement DevSecOps into The Pipeline Efficiently
Some Helpful Practices On How To Implement DevSecOps into The CI/CD Pipeline Efficiently:
The best way to ensure DevSecOps CI/CD pipeline integration is a success is to follow a few simple guidelines.
1. Collaborate with Developers, people committing to the idea is key. Security needs to be a shared responsibility, integrated from the start.
2. Automation drives innovation, automate as much as possible.
3. Focus on small frequent releases and development cycles fixing all security issues before advancing.
4. Continuation of everything and speed is key to DevSecOps Pipeline victory.
5. Crown a “Security Champion” who will be an advocate for DevSecOps culture within the organization.
6. Remediate in order of severity. Highest to lowest.
7. Once you get feedback, remediate, and do not let the same vulnerabilities come back.
8. Track performance thought the use of SLAs and KPIs.
I am certain there are a lot more, these are just a few we could think of off the top. So, if you are looking to embed security into the DevOps Pipeline give our DevSecOps engineers a call. Praetorian Secure has worked with companies who are large enterprise fortune 100 companies to lean startups with less than 100 employees, no matter the effort our experts know how to get the job done right. We develop custom services based on your needs and current infrastructure. You can count on Praetorian’s experts but do not take my word for it, set up a consultation to learn more and get a hassle free quote today.
About Praetorian Secure
At Praetorian Secure we take a sense of pride in the cybersecurity consulting and compliance services we deliver. The goal is to improve an organizations security posture while building confidence and understanding at the same time. Keeping important assets secure from threats since 2009. Praetorian Secure is a Service-Disabled Veteran-Owned Small Business (SDVOSB). Founded by two former U.S. Army Agents of the Certification Authority. Gaining momentum quickly they expanded their locations, adding a branch in South Florida. That is when we decided we wanted to be involved in helping companies achieve compliance or improve their cyber security in a more simplistic, hassle-free manner. Our service expertise includes Compliance Services, DevSecOps, Vulnerability Management, Cloud Security, vCISO, and more.
We have worked with companies across the globe, within varying industries to create a better/stronger/healthier security landscape. Including clients such as MetLife, Xerox, United Health, U.S. Army, Airforce, Navy, and more. We live in a world where threats never stop evolving and hackers do not take any days off – as responsible business owners/employees we must not ignore this reality. If you are interested in learning more please contact us via phone at +1 (855) 519-7328 or at info@praetoriansecure.com. Securing today, for a safer tomorrow!