When it comes to the question SAST vs. DAST: Which Application Security Testing Method Works Best? The answer is, “it depends” because this question cannot be accurately answered without some further info. Including, but not limited to what are we testing… a web app, mobile app, etc.? What is installed in your environment? Are you looking for white box or black box testing? Do you want to test source code or only test the execution of the application? What stage of the Software Development Life Cycle (SDLC) is your application in? These questions help narrow down which method will be best for your organization. Sometimes the best way is to take a hybrid approach to application security testing.
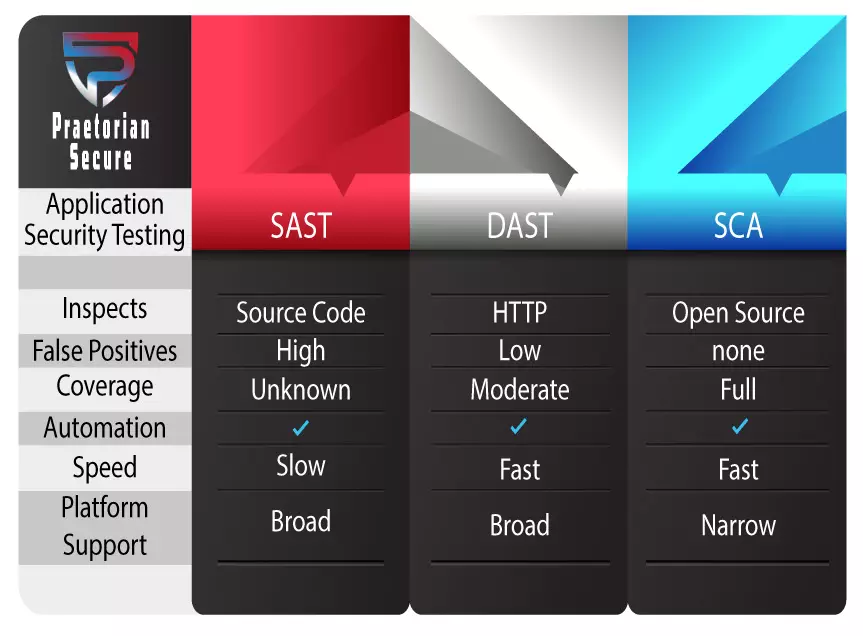
SAST
Static Application Security Testing (SAST) is one of the longest-running testing methods currently in use or otherwise known as white box testing. With SAST testing can begin early in the development process because you inspect an application’s source, binary, or byte code while at rest (non-compiled code). To elaborate, SAST tools test line-by-line, to expose weaknesses in the software before it is deployed. Inspecting static source code and then reporting on discovered security vulnerabilities.
Static testing tools can be applied to non-compiled code to find problems during development. For example, syntax errors, input validation issues, math errors, invalid or insecure references. Additionally, we can run the test with compiled code if applicable using specific binary and byte-code analyzers. Detecting vulnerabilities early in the development process can save your organization a lot of money in the long run. All things considered, testing early can be very beneficial for your organization and speed up the development process while in the same vein creating more secure code and coding practices.
Advantages of SAST
- Supports a wider variety of code/software than DAST and is scalable.
- Less expensive than DAST because you spend less time and money in the long term.
- Looks directly into source, binary, or byte code.
- Can focus on things other than just runtime environment, such as compilers, IDE, network infrastructure, etc.
- Finds theoretical issues not just known vulnerabilities can be more abstract.
- Quick results when testing pieces of code but not entire projects.
- SAST tools can integrate into your build pipeline with triggers and automation.
- Test at any stage of the SDLC, the earlier the better.
Disadvantages of SAST
- Traditionally it can be slow to execute depending on the number of lines of code.
- Can produce a high number of false positives.
- Just gives results does not provide actionable advice on how to fix it.
- Requires developer commitment to improving code security.
- Missing some context. Cannot identify vulnerabilities outside the application code, such as those defects that might be found in third-party interfaces.
- Complex for some organizations to use properly and effectively.
DAST
Dynamic Application Security Testing (DAST) tools use a black box testing approach. This means that you test for vulnerabilities “in the dark” or from the outside in as a hacker would attempt to do. There are many different commercial and open source DAST tools on the market today, but it comes down to using said tool correctly.
DAST tools are deployed on the application server, it involves hacking an actively running system. Dynamic tests are focused on runtime and environment issues in terms of security. Once the testing is completed, we compile a report containing security vulnerabilities found in the application. These are documented using The Common Vulnerability Scoring System (CVSS).
Black Box Testing
Black box testing is defined into two categories: functional testing and non-functional testing.
- Functional testing – performed to verify that all features developed are following the functional specifications and that it is performed by executing the functional test cases written by the QA team. During the functional testing phase, the system is tested by providing input and then we verify the output. Finally, comparing the actual results with the expected results and reporting on the findings.
- Non-Functional testing – is a testing technique that focuses on non-functional features and concentrates on the nonfunctional system attributes such as performance, memory leaks, or robustness of the system. To elaborate, these non-functional tests include performance, recovery, capability, security, and usability.
Preferably DAST should be executed against a system using a production-like environment for maximum accuracy and efficiency. For example, DAST testing tools may help find security vulnerabilities including:
- Query Strings
- Authentication Issues
- Memory Leaks
- Buffer Overflow
- Session Issues
- Data Injection
- Sensitive Data Exposure
- XML external entities (XXE)
- Broken Access Controls
- Cross-Site Scripting (XSS)
- Insecure Deserialization
These are just some examples, not a definitive list. Our experts customize the DAST tools to attack specified attack vectors that are relevant to your application.
Advantages of DAST
- Does not require source code and is language agnostic (not program language-specific).
- Takes a “hacker” or “real-world” approach.
- Fewer false positives than SAST
- Can identify all systems including middleware, web servers, and databases.
- Good support for manual testing.
- Easy and quick to retest.
Disadvantages of DAST
- Needs to be a “running” application to perform DAST.
- Typically done at end of SDLC, which can be more expensive to remediate vulnerabilities.
- May produce some false positives.
- DAST testing tool effectiveness relies heavily on the experts to write good tests.
- Supports less variety of software because the application must be running a certain way.
- Unable to isolate the exact source of a vulnerability in code and it may take longer to fix (without IAST).
SCA
Software Composition Analysis (SCA) is an application security testing method that helps development teams actively manage their risk. This method aims exclusively at the third-party and open-source components you’re using to build your application. Shifting to the left creating more secure development practices.
Our SCA tool translates SCA files and dependency files into NST files. Then we run your code through a variety of different engines to find vulnerabilities. When scanning our tools allow us to select rules or rules packs. These can be custom configured and then the project results file is generated and your SCA scan report is ready to review.
Bundling SCA with SAST is what we usually recommend based on our experience. In most situations, 70% – 90% or more of code in the modern application is comprised of different bits and pieces of open source. Also, the SCA tool we use is developer-friendly so your team will not mind using it. SCA tools typically have a software bill of materials (BOM) including the code base, dependencies, calls, and library links. This creates a checklist that can be used to enforce and maintain higher-quality coding standards.
Advantages of SCA
- Automate security within your CI/CD pipeline.
- Creates discipline among developers.
- Simplifies software review process.
- Helps prioritize fix actions.
- Using tools that can accurately detect SCA vulnerabilities.
- Reassurance of control over open-source code used in your applications is proven by testing.
Disadvantages of SCA
- Visibility is clouded when open-source code is embedded into an app’s codebase.
- Does not understand dependency logic.
- Open-source code is not maintained forever.
- Can slow down development process if done incorrectly.
 The Best Application Security Testing Method
The Best Application Security Testing Method
Every testing tool and method used will have advantages and disadvantages such as every other facet of our lives. As your trusted experts, we will gather all the information needed and then provide a recommendation based on how we believe your organization can improve.
A combination of SAST and DAST works best in most cases. Otherwise known as a Hybrid Application Security Testing (HAST) approach. For example, if you are in the early stages of the SDLC use SAST to begin analyzing your code. Then, after you have the running application, implement DAST to ensure it is safe before presenting it to real-world users. Additionally, you can cross-reference results from SAST and DAST tools to identify which potential vulnerabilities (identified by SAST tools) are exploitable (identified by DAST tools). This allows your team to gain the highest level of threat insight to make the best decisions moving forward.
It is safe to say when it comes to choosing which testing method is best for application security testing (AST) it is unanimously decided a Hybrid Application Security Testing (HAST) approach works best. It may seem like an unnecessary amount of time and budget invested but nothing can replace the feeling of knowing your flagship application is safe and secure.
Furthermore, that your development teams will continue to use better, more secure coding practices long into the future. SAST and DAST both have widely different uses and benefits. It is like comparing apples to oranges, they are just not the same thing. As it may seem a difficult task to implement this, but our experts help reduce your team’s effort. Also, you do not want to experience a data breach or security threat down the line that could cripple your company’s reputation, growth, and revenue. Contact our team to find out just how simple it is to start integrating AST tools into your SDLC pipeline today!
About Praetorian Secure
At Praetorian Secure we take a sense of pride in the cybersecurity consulting and compliance services we deliver. The goal is to improve an organizations security posture while building confidence and understanding at the same time. Keeping important assets secure from threats since 2009. Praetorian Secure is a Service-Disabled Veteran-Owned Small Business (SDVOSB). Founded by two former U.S. Army Agents of the Certification Authority. Gaining momentum quickly they expanded their locations, adding a branch in South Florida. That is when we decided we wanted to be involved in helping companies achieve compliance or improve their cyber security in a more simplistic, hassle-free manner. Our service expertise includes Compliance Services, Cybersecurity Consulting, Security Testing, vCISO, and more.
We have worked with companies across the globe, within varying industries to create a better/stronger/healthier security landscape. Including clients such as MetLife, Xerox, United Health, U.S. Army, Airforce, Navy, and more. We live in a world where threats never stop evolving and hackers do not take any days off – as responsible business owners/employees we must not ignore this reality. If you are interested in learning more please contact us via phone at +1 (855) 519-7328 or at info@praetoriansecure.com. Securing today, for a safer tomorrow!