Scripps Health Ransomware Attack: The Healthcare Industry is Under Siege, Again…
Welcome to the real life, “worst-case scenario” as an InfoSec professional. As the VP of Information Security you are responsible for keeping the company in good cyber health. Lets say that your currently working for a healthcare company that was just targeted in the latest ransomware attack. Before you know it, all technical equipment is malfunctioning, all company infrastructure is down, and patient information has potentially been compromised. You will be faced with many tough decisions in the next 24 hours and according to how prepared your organization is for a critical cyber threat will determine how stressful or simple each decision will be.
Now it is time to act what do you do first? Hopefully, the answer is implementing your disaster recovery plan immediately. Then, contact your critical staff and stakeholders and switch over to back up systems until all critical systems are restored and adjust accordingly. As cybersecurity experts, we never recommend paying cyber criminals a ransom. Although, some companies who do not have a disaster recovery plan in place might have to weight their odds. If your organization in need of 3rd party Cyber Security Services Praetorian Secure can help. Just as oral hygiene is important to keep other body organs healthy, like you heart. Cyber hygiene works in the same way, but for your overall business health, but first lets learn more about this ransomware attack.
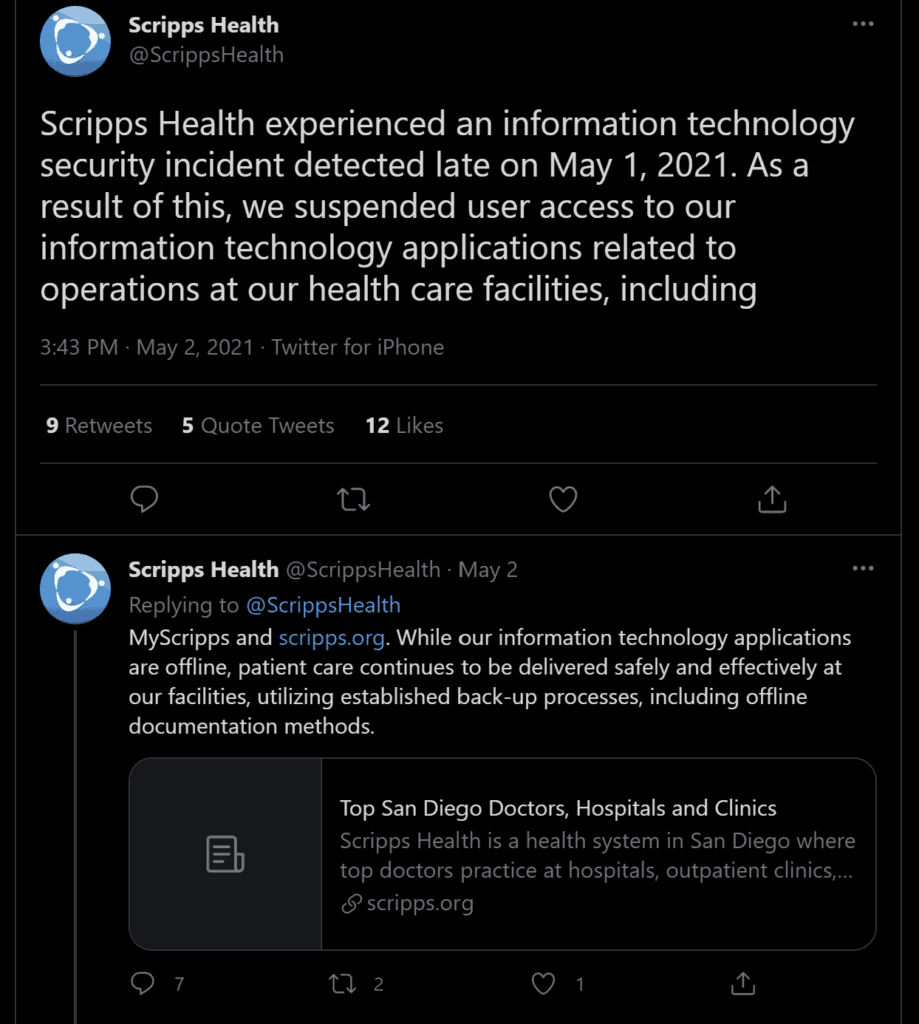
May 2, 2021 Scrips health sent an update via twitter:
Friendly Neighborhood Ransomware Attack
On May 3, The San Diego Union-Tribune indicated that, “information systems at two of Scripps’ four main hospitals were infected, including backup servers in Arizona.” Scripps Health released a statement saying they had been a victim of a ransomware attack and plan to alert the authorities. Also, they were diverting critical care over the weekend, the MyScripps portal was down, Scripps.org was down, and they had to divert to an EHR contingency plan due to the attack.
According to a study, Evidence-based Contingency Planning for Electronic Health Record Downtime, “Downtime risks include delay of care, increase in medical error, and disruption in communication. Effective downtime contingency plans can reduce these risks. Computer simulation can assess the performance of various downtime contingency plans and can inform and improve current practice” (Wernz). The point is not to decide if Scripps was unprepared or did not act appropriately. It is to gather positive information that other companies can learn from to create better cyber hygiene. There were just small crumbs that did not get addresses and ended up becoming a big deal. Sometimes companies pay for even the smallest mistakes.
What Can We Learn About Cyber Hygiene?
“We want to reassure our patients that our physicians and employees are well-trained and thoroughly prepared to respond to this sort of situation so that we can continue to care for the community’s health care needs” (Scripps). Scripps handled the situation very well from a public relations (PR) standpoint. Scripps failures could have been possible for anyone. Also, 99.9% secure means there is a slim chance something can go wrong. Highlighting what happened and how it can be prevented in the future is the best way to educate other organizations. Once there is an investigation this information should be shared with the public. This type of mindset is what we need as a technology community. To share our experiences and learn as a community. Moreover, it does not hurt to get a third-party involved to perform some additional testing and assistance if needed. Please do not hesitate to contact us or another expert to learn more.
Does My Organization Have “Good” Cyber Hygiene
If your comfortable where you stand today, is it because you have A.) taken the time to understand what a solid disaster recovery plan requires or B.) because your too afraid to dive deeper and uncover the truth about the inadequacies in your process & procedures and most certainly what controls are in place to prevent negligence or bad actors. When it comes to creating a backup strategy first determine recovery time objectives and recovery point objectives for each data source and application. What are my most critical systems and how much would it cost me if they were down for x hours? Then you can decide what type of backup plan is necessary for different sections of your organization. Then create and document your new process and plan. Your now on your way to becoming a disaster recovery aficionado.
Testing Options, Best Practices, & How To Report A Ransomware Breach
It is best to test in a way that is most realistic for your organizations budget and risk appetite. Some popular ways to complete a disaster recovery test are:
- Paper – write it out and have other read and verify it makes sense
- Walkthrough – like a fire drill, act it out to ensure everything works when it is important
- Computer simulation – run calculated test to ensure most efficient strategy is in place that meets business needs
Best practice is to implement and enforce access with rules and counter measures in place to prevent any threat intentional or unintentional. Finally, remember the FBI is requesting victims reach out to their local FBI office and/or file a complaint with the Internet Crime Complaint Center, at www.IC3.gov, with the following ransomware infection details (as applicable):
- Date of Infection
- Ransomware Variant (identified on the ransom page or by the encrypted file extension)
- Victim Company Information (industry type, business size, etc.)
- How the Infection Occurred (link in e-mail, browsing the Internet, etc.)
- Requested Ransom Amount
- Actor’s Bitcoin Wallet Address (may be listed on the ransom page)
- Ransom Amount Paid (if any)
- Overall Losses Associated with a Ransomware Infection (including the ransom amount)
- Victim Impact Statement
Key Takeaways
In conclusion Scripps Health will most likely be reevaluating their policies, procedures and more importantly controls in place to prevent an incident like this from occurring. All too often organizations grant too high of privileges to employees who do not necessarily need them. Or they forget about something that someone did a long time ago and forget it even existed before it become the source of a cyber threat. We have worked with companies across the globe, within varying industries to create a better/stronger/healthier security landscape. If you are interested in learning more about our Cyber Security Services please contact us via phone at +1 (855) 519-7328 or at info@praetoriansecure.com. Finally, we hope this information was useful and do not forget to always practice good cyber hygiene!
n.a. “’Security Incident’ Forces Scripps Health to Scramble, Take Patient Services Offline.” Times of San Diego, 3 May 2021, timesofsandiego.com/business/2021/05/02/security-incident-forces-scripps-health-to-take-patient-services-offline-as-officials-rush-to-repair-damage/
Wernz, Christian. “Evidence-Based Contingency Planning for Electronic Health Record Downtime – Final Report.” Virginia Commonwealth University, 2018